Tableau Conference 2025 | Know Before You Go
If you’re a data enthusiast, analytics professional, or just someone curious about Tableau’s latest innovations, the Tableau Conference 2025 is your...

More and more we are seeing companies offer at least a portion, if not all, of their services in the cloud. The trend has been growing due to the power and flexibility that cloud computing can provide for modern big data analytics.
Cloud computing was developed to allow for compute resources to be accessed on demand via the internet. The services available in the cloud include data storage, databases, servers and more. I would say one of the most appealing aspects of the cloud platforms is that most services are pay-as-you-go pricing models, which allows you to scale up or down as needed!
Snowflake is a cloud data warehouse with unique architecture developed for the cloud. They utilize cloud computing for all the compute and storage needs. There is no hardware to install or manage and Snowflake takes care of any maintenance and updates themselves.
After learning more about Snowflake and the cloud capabilities that were available, my biggest concerns and questions were related to the security of the data that would be stored in the cloud. I wondered how you could avoid sensitive data being compromised if it no longer sat on-premise.
I recently developed a data warehousing solution utilizing Snowflake. These are the strategies that I, as a site role SYSADMIN, utilize and enforce to make sure that the data is secure and protected throughout the whole process.
Since the platforms can be accessed via a web link, I knew it would be important to have strong user authorization in place. Implementing specific access controls based on user site roles has been an effective way to ensure that the data is only accessed by authorized users. Each user that has a login is assigned to a site role that corresponds to what they are allowed to see. Snowflake comes with several default roles out of the box: ACCOUNTADMIN, PUBLIC, SECURITYADMIN, SYSADMIN.
These default roles have different privileges that allow them to take certain actions, for example the SYSADMIN role has CREATE ROLE privileges, so they are able to create new roles. Once created, each role can then be granted the privileges to access only the databases/schemas/views that they should be utilizing. The privileges granted could allow roles to delete an object, modify an object, or just execute a select statement on the object. A common example would be giving the business users the site role of ANALYST, where they would have the ability to execute select statements on the views they need to report on. Strong passwords and multi-factor authentication are also used for each user.

Another recommended method to ensure secure authorization is creating Network Policies within Snowflake. You are able to create a whitelist of IPv4 Addresses that will have access to your account. This can give you the peace of mind that only trusted addresses will have access to the site. You can also block IPv4 Addresses if necessary, however this is not required as any addresses that are not on your whitelist will be automatically blocked. Be sure to test these policies as you develop them.

One important step in maintaining the security that has been implemented so far is having a strategy for monitoring the activity on your account and having alerts for any activity that is out of the norm. One way to monitor activity in Snowflake is to set up alerts and limits through the Resource Monitors. You can be alerted when a certain amount of credits have been used on your account, and also automatically suspend the account after a certain point.
I would also recommend having a process in place to monitor the query history and the active sessions on a regular basis, in order to check for additional unusual activity.

After implementing these three measures, I felt more confident that the data was secure in the cloud. If you want to learn more about Snowflake’s security features, you can check out Snowflake’s official documentation here.
If you have any questions on how to get started on your cloud analytics journey, send me a note at megan@godatadrive.com!
-2.gif)
If you’re a data enthusiast, analytics professional, or just someone curious about Tableau’s latest innovations, the Tableau Conference 2025 is your...

Tableau Plus is the new premium offering from Tableau, a leading data visualization and business intelligence platform. It builds upon the...
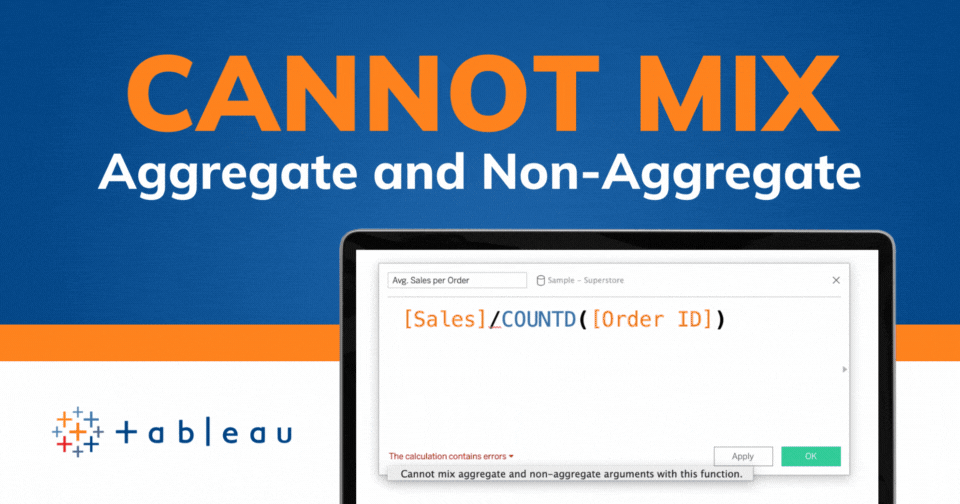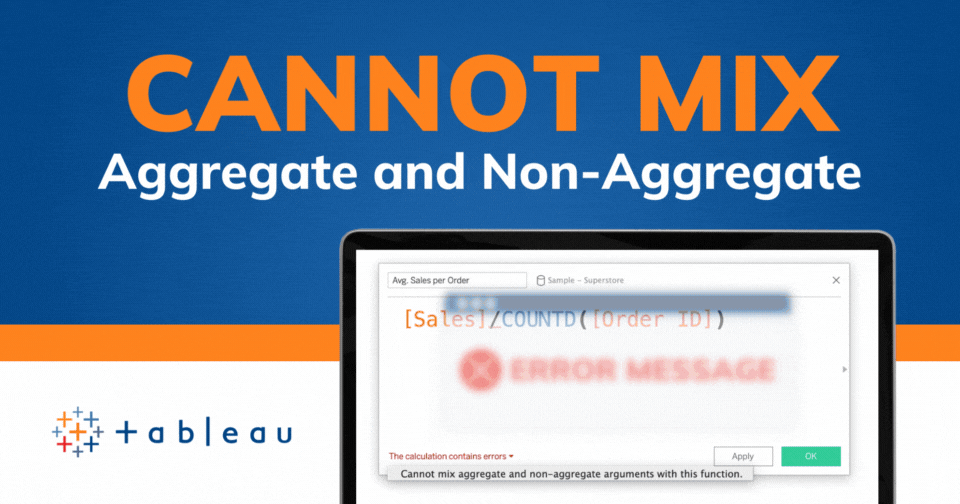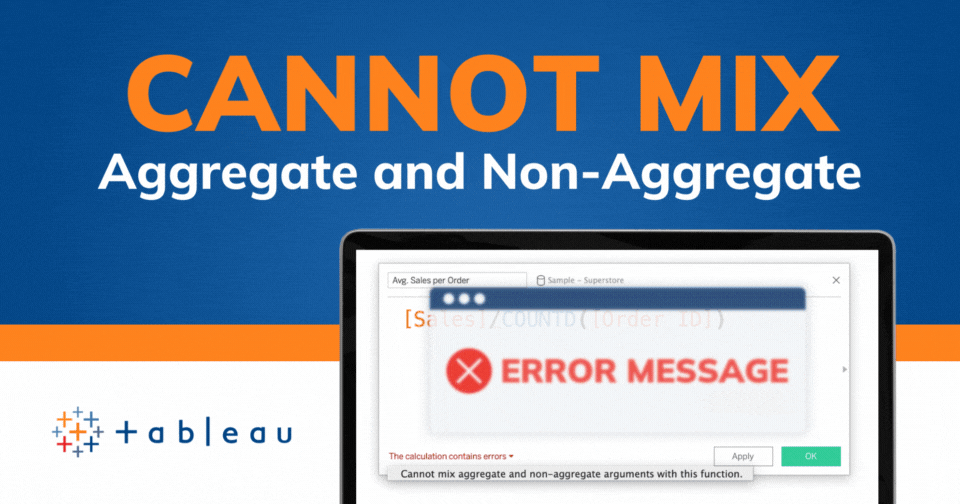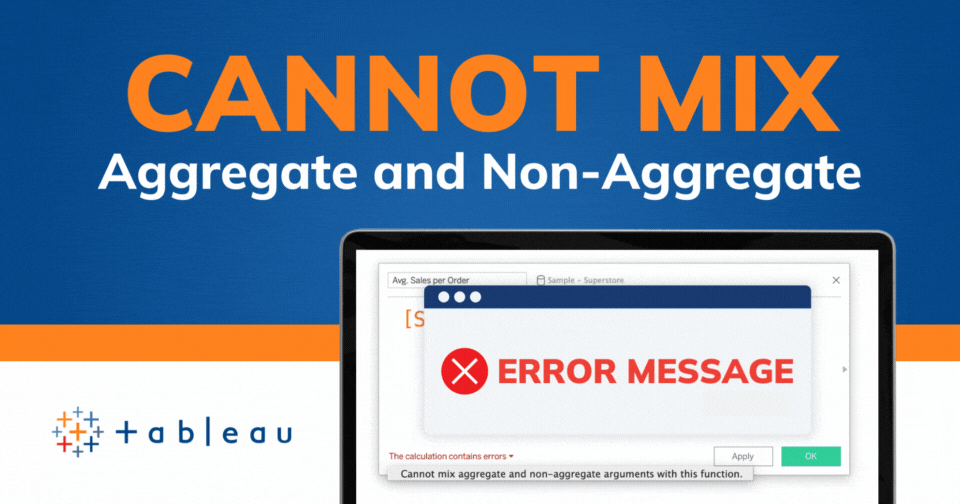
If you've spent any time working with Tableau, you've likely encountered the dreaded "Cannot Mix Aggregate and Non-Aggregate Arguments" error. It's a...